Hi @oleg-vyalyh and @mark-piller!
I decided to start from scratch and stuck again. I created a new table and implemented a simple service, that returns the array with the data of that table.
I tried to configure permissions (Auth role has access to retrieve the data, the Customer role has access to retrieve the data).
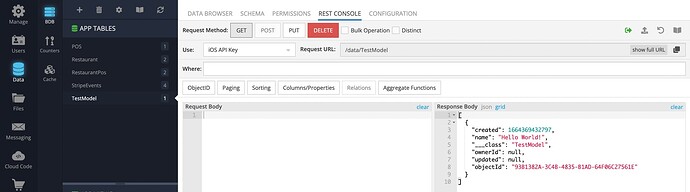
The problem occurs when “Customer” role uses the direct DB API. The response contains the data
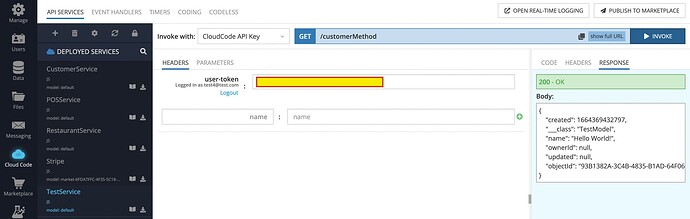
The cloud code returns the expected result:
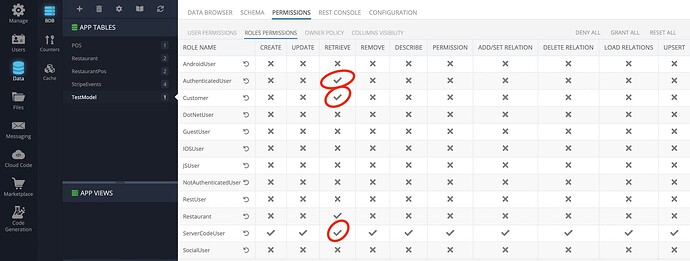
The table has the following permission configuration:
If I deny access for the Customer role, the cloud code returns empty response, and Direct access continues working.
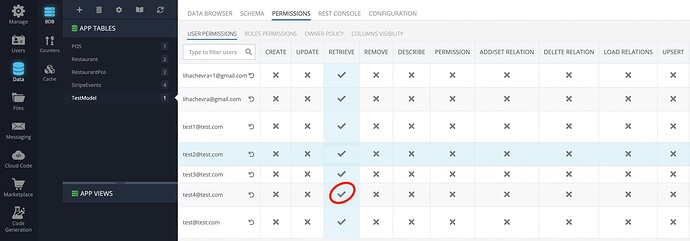
If I deny access for the particular user (test4@test.com in the current example), the response contains no data in any case.
What needs to be changed to close direct access to the database?
Please use test4@test.com/123123qwe user for testing purposes if need it.
Thank you!