Hi,
I’m using Backendless Cloud. I have a trusted server environment, and I want to be able to access data tables with admin-like permissions, so that I can read and write any data for things like generating reports.
What’s the recommended way to do this?
What I’d really like is to be able to generate a secret API key that when passed along with any request allows admin permissions. I can’t see a feature like this in your docs.
I can see two ways:
-
Create a user, and assign that user broad permissions to every data table. Then “log in” as that user to get a user token, and submit the token along with every request. My main issue with this is that my server is stateless (I’m running on AWS Lambda), so I’d need to add another data storage service like Redis in order to persist the token between requests.
-
Use the “Administration and Management API” that I’ve seen discussed on this support forum. But I can’t find any reference to this in the current docs, has it been discontinued? And in any case, it looks like this API requires a login too, so the same problem of persisting the token applies.
Thanks,
Bernie :o)
Hi Bernie,
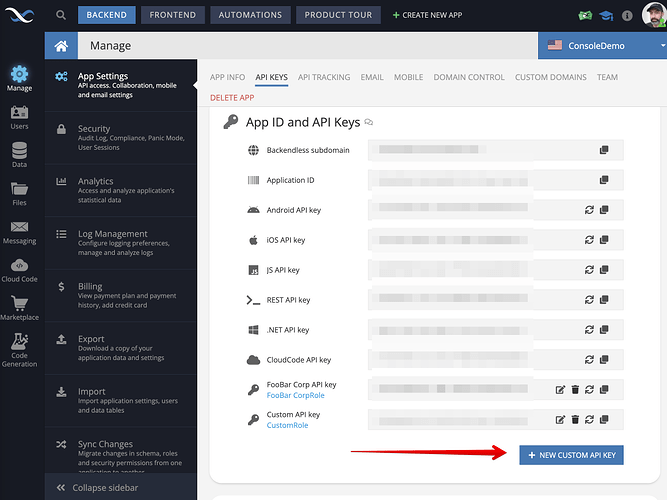
Here’s another option for you - create a custom API key as shown below:
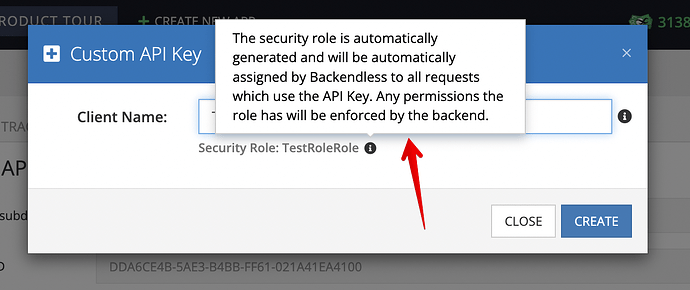
When you create a key, a new security role is also created:
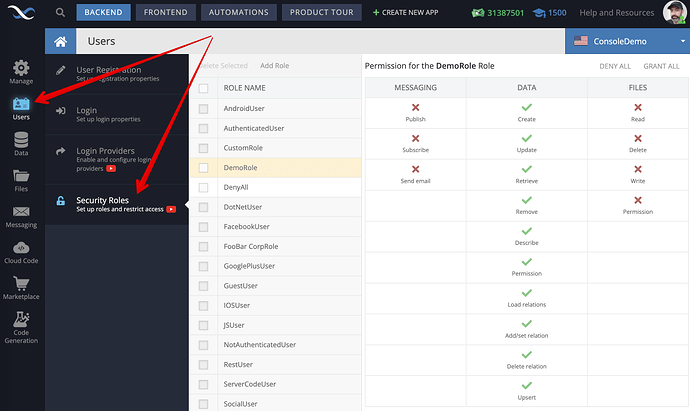
Whenever you use the API key to make invocations, the corresponding role is automatically used by Backendless. You can configure role’s permissions on the following screen:
Additionally, you can assign specialized permissions to the role for every table/file directory/messaging channel, etc.
Hope this helps.
Mark
That was weird, I was still getting undefined on my mobile.
The issue was one of the values for the function, I had to delete the value and recreate it under a different name for it to work.
Even when I deleted it and recreated using the same name, it would return undefined only on my mobile.
Sorted now though, thank you
Thanks Mark. I had a go with custom API keys, but hit an issue.
In order to allow access through a custom API key I need to enable both MyApiKeyRole and NotAuthenticatedUser in the Roles Permissions for my tables (because API requests using my custom key don’t have a user-token).
But enabling NotAuthenticatedUser also allows unauthenticated access through other APIs, and since these have public API keys (as in you can find them in the source of the client apps) it allows anyone to access the database using one of the public API keys even if they don’t know my secret key.
Is there a way of allowing broad unauthenticated access with the custom API key, but not granting the same permissions to unauthenticated users on the other API keys?
Sure. Try denying access to the RestRole, AndroidRole, etc roles. This will disable access to any non-authenticated user who uses the corresponding API keys.