We noticed that the login sometimes does not work since a couple of days.
I tried to login several times with several browsers and it failed about 1 out of 3 times with the following error:
https://s3-eu-west-1.amazonaws.com/uploads-eu.hipchat.com/62625/433014/VESNrBGjvVlHWAt/upload.png
It always failed in Firefox.
According to a client this did not work the whole weekend, which is unacceptable.
Please update your CORS settings to * to allow all cross domain requests.
Update!
I noticed that the error is actually maybe not related to CORS, but your SSL certificate that is revoked!
https://api.backendless.com/
Firefox shows the error message: sec_error_revoked_certificate.
Other browsers seem to work
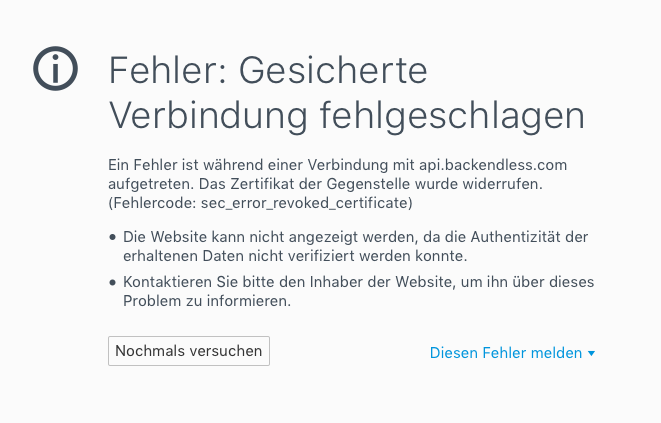
This is a problem specific to Firefox. You need to uncheck the following checkbox in settings:
http://support.backendless.com/public/attachments/2c2797edec5049f965475f9f96fa5d74.jpg</img>
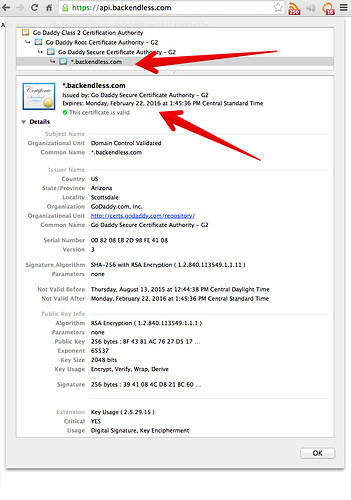
We have no control of the OCSP servers firefox uses and they clearly have outdated information about our certificate, which you can easily confirm is completely valid:
http://support.backendless.com/public/attachments/af7fbefff5801b427f3fc3c8eea22b0d.jpg</img>
Not possible. I cannot force users to change settings in their Firefox installation, it has to work for every visitor.
I can see that the certificate seems to be valid, but yet it is a problem with your SSL certificate that OCSP fails.
You are asking us to change something that we have no control over. How can we change the way Firefox works with OSCP servers? It is not our browser and not our servers. All other browsers accept our certificate just fine and you can see that yourself.
Have you considered contacting the Mozilla team to ask what they can do?
The way I see it, Backendless does not work with Firefox, which should make this your priority concern immediately. I actually have way less control than you in that matter.
The problem is not how Firefox checks the certificate, the problem is that for some OSCP servers it is considered revoked. You should contact the GoDaddy support in that matter and request a renewed certificate or check if their service might handle something faulty.
https://www.ssllabs.com/ssltest/analyze.html?d=api.backendless.com
Hey Mark,
please get in touch with GoDaddy asap, this is definitely a problem with them.
Use any online ssl certificate validator and they will tell you the same thing:
https://s3-eu-west-1.amazonaws.com/uploads-eu.hipchat.com/62625/433013/Aj03chGAvNMdJIe/upload.png</img>
https://www.digicert.com/help/
https://s3-eu-west-1.amazonaws.com/uploads-eu.hipchat.com/62625/433013/Reiyog7VTWgIbmn/upload.png</img>
https://ssl-trust.com/SSL-Zertifikate/check
As a matter of fact, the information also just propagated to Chrome Canary’s OSCP Directory and thus I am sure many more users are going to experience the problem we are facing right now over the next few hours:
https://s3-eu-west-1.amazonaws.com/uploads-eu.hipchat.com/62625/433013/WjQEeEmB9D5DWX2/upload.png</img>
Ok, we will re-key and regenerate the certificate. I am not sure if it will help, but we will try.
We made the changes, could you please verify on your side?
The SSL certificate change works now in Android mobile application, REST application, Firefox and Internet Explorer.
NOTE: If performing SSL public key pinning validation, extract the public key from api.backendless.com.
Fabian and Mathis, can you please confirm if the problem is fixed for you?
The problem is fixed
Appears that the SSL certificate has changed again by using the previous SSL public key before the recent SSL certificate renewal.
Can you verify this?
Nothing has changed on our side. It shows the same public key that I sent you the other day in a direct email.